CloudSEK, a contextual AI digital risk platform, has uncovered a concerning incident involving a threat actor promoting a Telegram bot that claims to provide access to the personal information of individuals who registered for vaccines through the Cowin Portal in India. This article provides an in-depth analysis of the incident, explores the motives behind it, and discusses the potential impact on affected individuals and necessary mitigation measures.

Understanding the Context:
CloudSEK’s XVigil platform detected a threat actor advertising a Telegram bot offering personally identifiable information (PII) data of Indian citizens who allegedly registered for vaccines through the Cowin Portal. However, it is crucial to note that the threat does not have access to the entire Cowin portal or its backend database. Instead, the information is believed to have been obtained through compromised credentials.
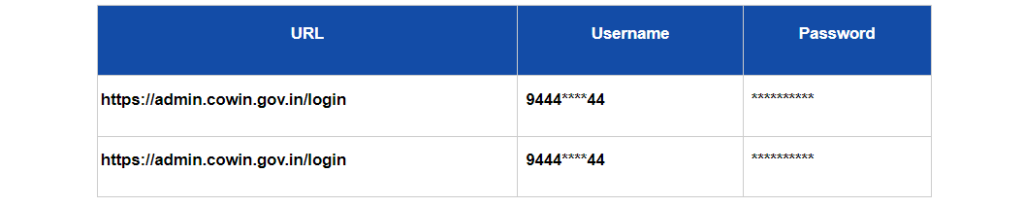
Incident Details:
On March 13, 2022, an individual on a Russian cybercrime forum made a claim of compromising the Cowin database in the Tamil Nadu region. However, upon further investigation, it was discovered that the breach was actually linked to a health worker rather than a direct compromise of the Cowin Infrastructure. The Telegram bot mentioned in the media exposed personal information, including names, mobile numbers, identity proof details, identification numbers, and the number of completed vaccine doses.
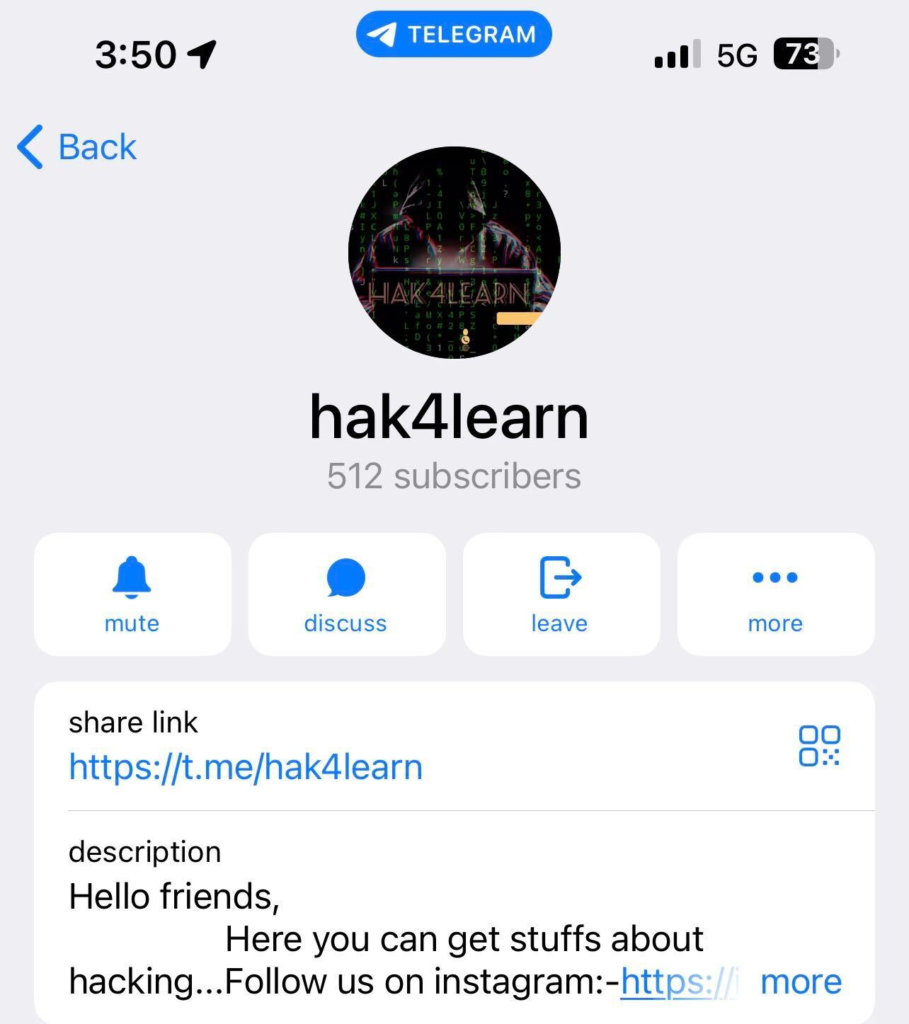
Analysis and Attribution:
The Telegram bot, known as Covid data bot, was offered through a channel called hak4learn, which frequently shares hacking tutorials, resources, and bots. Initially available to all, the bot was later upgraded exclusively for subscribers. The upgraded version of the bot provided PII data based on inputted phone numbers, including Aadhar card numbers, Pan card details, voter ID information, gender, and vaccination centre names.
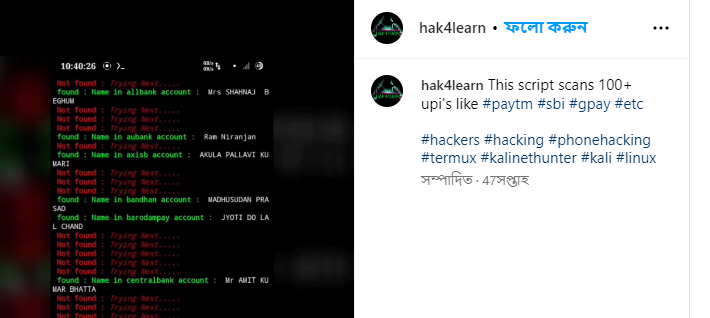
Threat Actor Profile and Rating:
Based on an Instagram post in 2022, an account associated with the threat actor offered scripts exploiting UPI payment gateways, indicating a non-Russian origin. The threat actor has a moderate reputation, frequently engaging in activities to monetize methods and data.
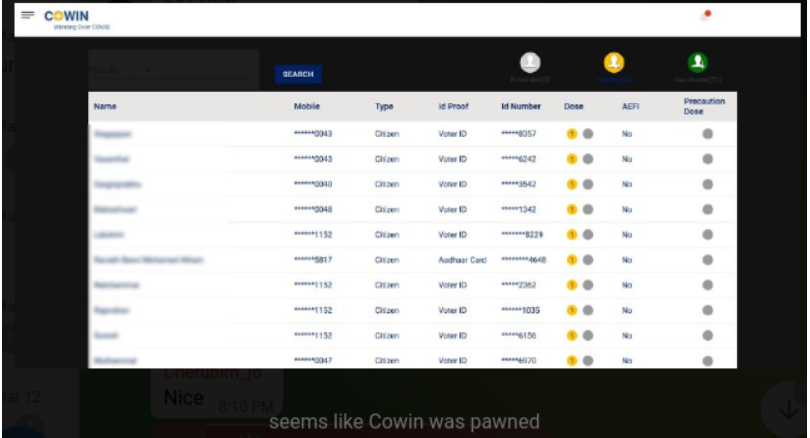
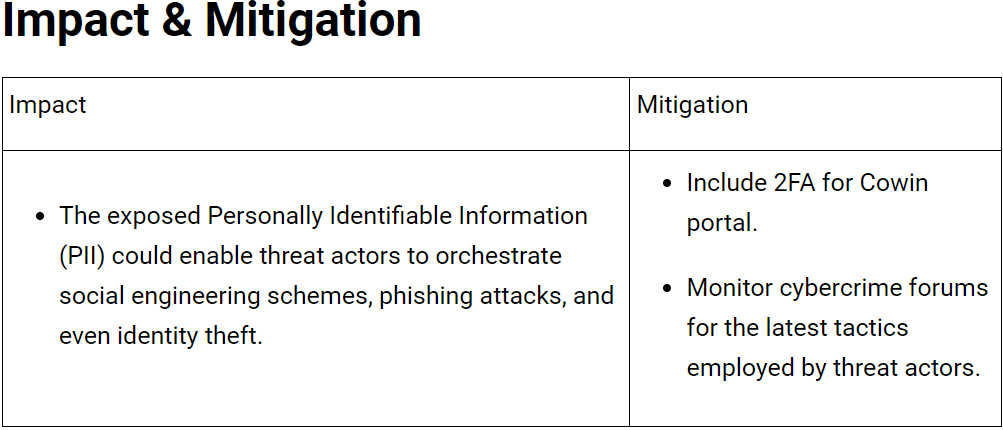
Impact and Mitigation Measures:
The exposure of personal data from the Cowin Portal raises concerns about potential risks such as social engineering schemes, phishing attacks, and identity theft. To mitigate these risks, it is recommended to implement two-factor authentication for the Cowin portal and actively monitor cybercrime forums to stay updated on emerging tactics employed by threat actors.
The discovery of a Telegram bot promoting access to personal data from the Cowin Portal underscores the need for robust security measures and heightened vigilance in safeguarding sensitive information. Individuals and organisations must take necessary precautions and remain informed about evolving threats to protect themselves from potential risks associated with data breaches. It is imperative to prioritise data privacy and security to ensure the well-being of individuals and maintain trust in digital platforms and services.
